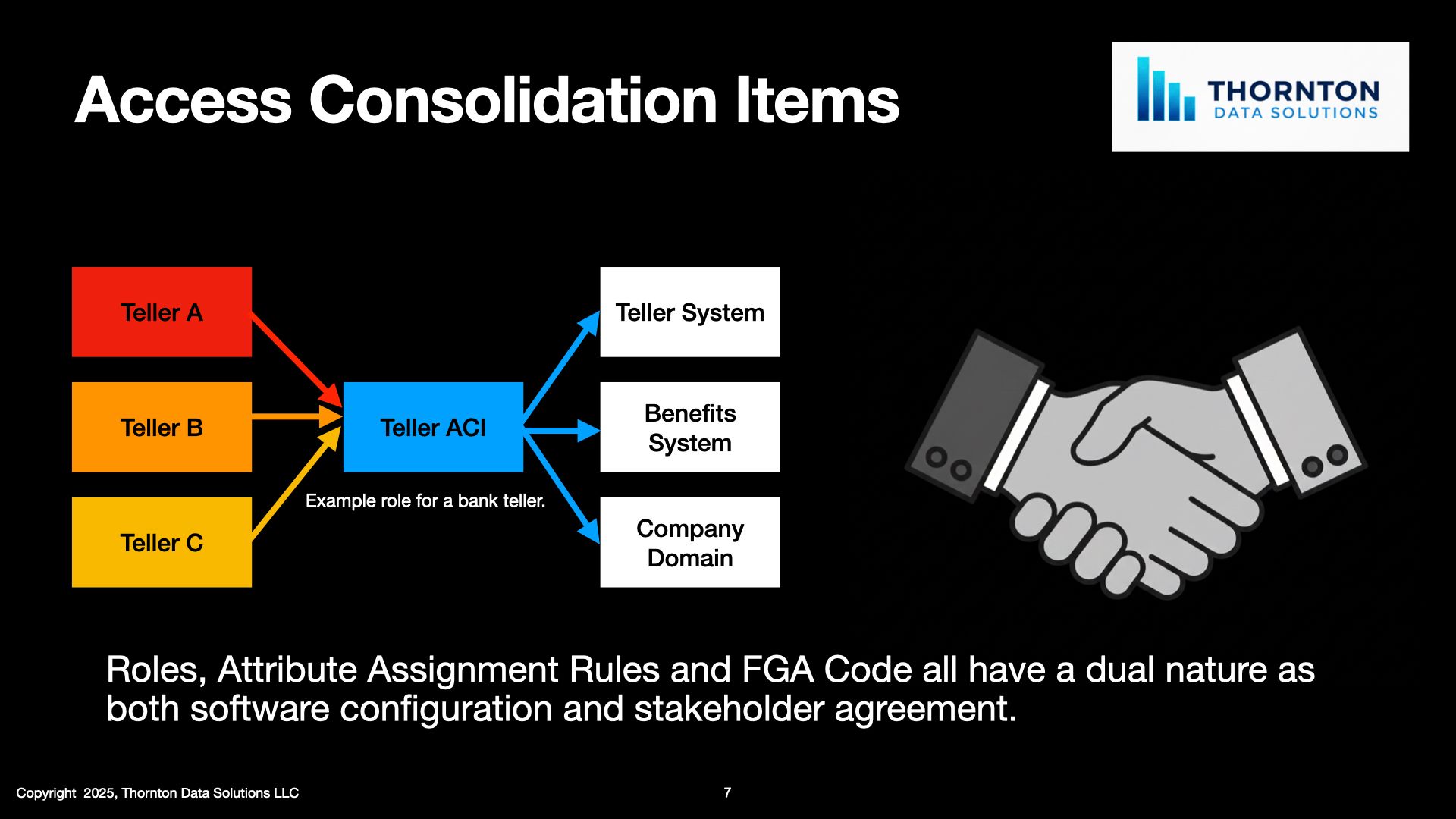
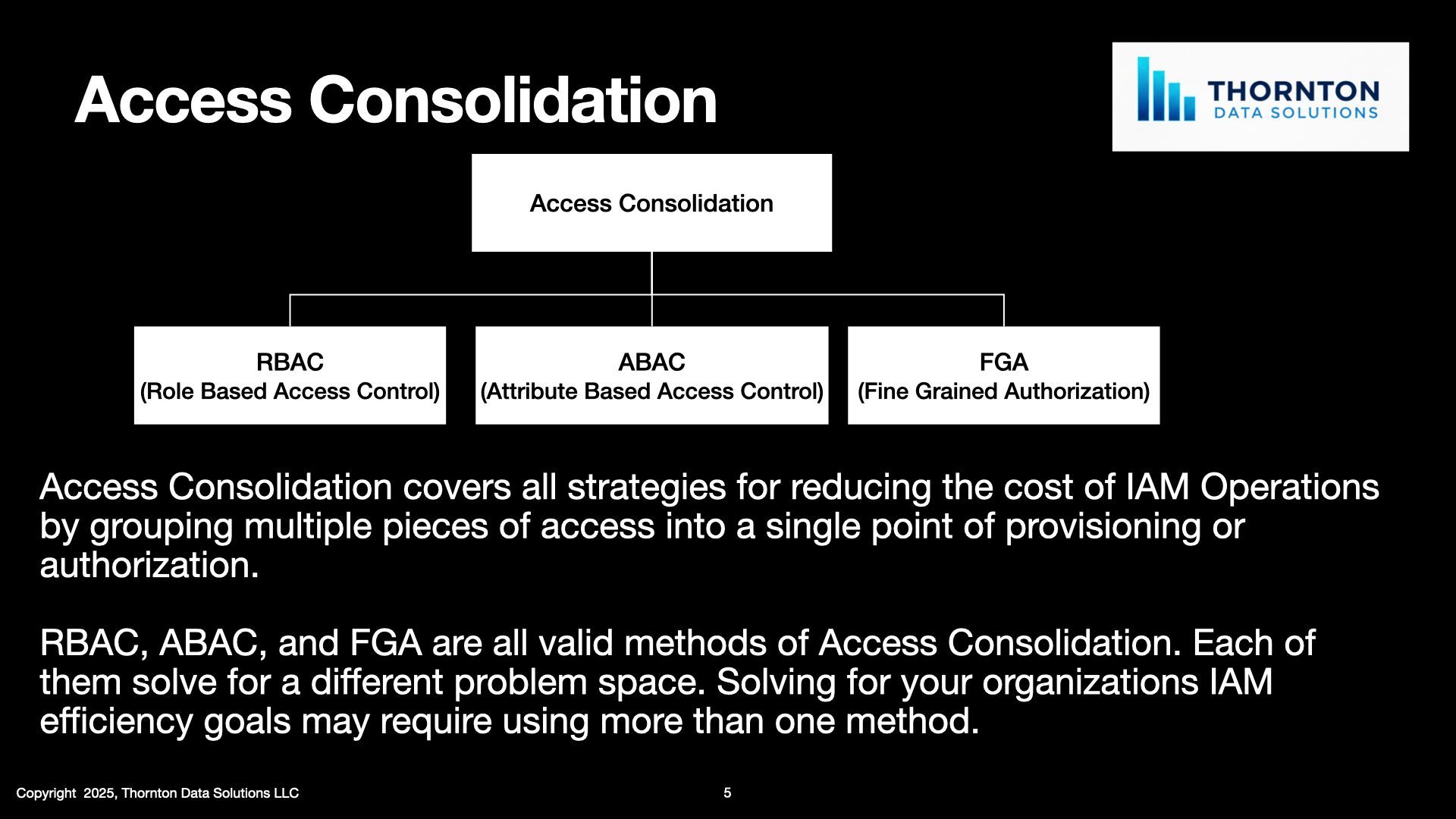
Roles are social, so what?
Access Consolidation has a social component, so what?

In a previous blog post I started expounding on the topic of what makes RBAC (and all Access Consolidation) difficult. One of the most significant reasons for this is the hidden social aspect of Access Consolidation. Because tool creators want you to buy their toolsets they do not mention this work, and unless you've performed an Access Consolidation effort before you may not be aware of the social effort it takes. So what difference does it make that there's a social component to this work?
1. There is no purely technical / software solution to this problem.
There are a number of providers of Role Mining, IGA and Authorization solutions that feature their own takes on how to solve the access consolidation problem. They are all relatively easy to use in terms of how they acquire and present data and capture the decisions made about implementation. Most of them are capable of demonstrating a sample Access Consolidation Item creation in a couple of minutes. The reason this demonstration takes minutes while RBAC projects can take weeks or months is because they skip over the part where the IAM team has to build consensus on the structure and content of their roles. This part is glossed over for a pretty simple reason: it doesn't happen in their tool, it happens in person, it's a conversation with your colleagues.
2. You will have to have technical IAM discussions with people who are not IAM professionals.
Roles change the behavior of access request and certification. Done properly, people who are used to requesting a dozen things for each of their new employees will only have to request one or two. They are still responsible for the access of their employees however, and they're going to need to provide their consent on both the creation of the role and its contents. This means they need to be sold on the benefits of the solution as well as the technical details of the analysis that suggests what the contents should be. While this information will make sense to your IAM Team, remember that the colleagues you're working with will at times be from very different disciplines within your organization. Your finance team, manufacturing team and customer service representatives for example all have very different perspectives on the business.
If your team is not used to communicating with people who are outside of the cybersecurity / application owner space you may want to consider developing developing or acquiring that capability. The ability to put a value proposition for a role into words that a doctor or a banker can understand will make it a lot easier when you go to review its contents with them. Familiarizing yourself with your access customers concerns will make this process much smoother.
Some things to keep in mind during these conversations:
- The access names that your IAM team uses may not be the ones that your colleagues are familiar with. If your IAM team does not have human legible names for access in your upstream systems you may want to generate those prior to embarking on an Access Consolidation Program. Managers in your HR department for example might not know the DN of the group they're all in that grants them access to their fileshare. Other additional access metadata that may need to be cleaned up include: access descriptions, security levels or owners.
- If you have had particularly contentious conversations with organizational leadership as a result of previous access certifications or access request issues you should consider how best to broach the subject of creating an Access Consolidation Item for them. If they're unhappy with the amount of effort it takes to meet their compliance requirements and/or request access for their people then lead with the reduction in effort. If they're defensive about how previous access certifications have turned out consider working with their trusted peers first in order to generate a success story that can be shared with them.
3. Your piece of the organization is about to become a lot more visible.
An Access Consolidation program is when the IAM Team transforms from a background piece of the Cybersecurity team into a trusted partner that returns value to the organization. While the reduction in risk that a well run Identity Provider provides is certainly important, an Access Consolidation program allows the IAM team to provide something even more tangible: an improvement to a company's bottom line. To do this the IAM team will have to engage with the rest of the organization. This is when your IAM team goes from being a background maintainer of a niche cybersecurity tool to a trusted partner that enhances your business.
If you're considering undertaking any kind of Access Consolidation project including starting an RBAC Program and want to make sure that you return as much value to your organization as possible please reach out to us at john@thorntondatasolutions.com and we'll schedule a complimentary strategy session to get you started on the right foot!